We Are Offering All Kinds of IT Solutions Services
Passive Networking
We undertake to design Data and Voice Cabling solutions using a combination of UTP and fiber. With combined experience, our crack design team produces an optimal solution.
Active Networking
With a dedicated team of experts and certified network engineers, we have a command on creating or configuring the highest level of routing and switching protocols over any new or existing network by using various brands of Routers and Switches.
Firewall
All customers irrespective of size need to protect themselves from cyber threats. A firewall is a barrier or shield which works to prevent unauthorized access to and from a private network, enhancing the security of devices connected to a network like the Internet or a Local-Area Network. We always recommend internet gate-way level control using Firewall appliances.
Wi-Fi
Wi-Fi and its centralization with a range of various brands for SMB to Enterprise level.
Storage
We have exposure to NAS and SAN technologies to save and store the data securely.
Servers
We do supply and installation of towers, racks and blade servers.
Data Centre Solutions
We provide comprehensive solutions for Data Centre comprising of smart racks, cabling components copper and fibre, racks, PDUs, Switches, flooring, ceiling, etc.
Video Conferencing Solutions
Point-to-point and multipoint video conferencing is a connection between two different locations. We provide VC�s solutions according to customer requirements.
Surveillance
It is used to do Monitoring of behavior, activities, or information for the purpose of influencing, managing or directing. We deal with high-end video surveillance solutions that stand apart with their uncompromisingly reliable, intelligent solutions that can be expanded without limits and which provides long-term investment security.
EDR
Endpoint detection and response is an emerging technology addressing the need for continuous monitoring and response to advanced threats. One could even make the argument that endpoint detection and response is a form of advanced threat protection.
Multi Factor Authentication
Multi-factor authentication is one of the most effective tools which is used to prevent an adversary from gaining access to a device or network and accessing sensitive information.
VPN
A VPN, or Virtual Private Network, allows you to create a secure connection to any secured network over the Internet. VPN shields your personal information from the interference of third-parties and hackers on public Wi-Fi, ISPs and other local networks.
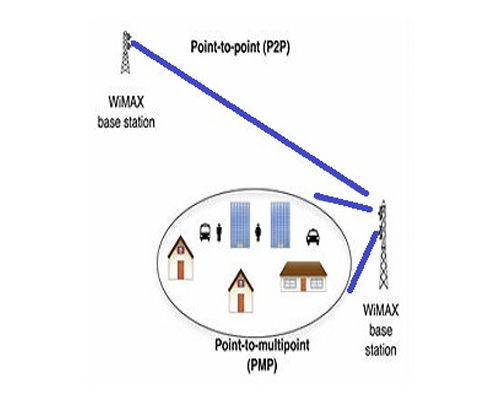
PTP (Point to Point)/PTMP (point to multi point) solution on RF
Point-to-point communication is a type of communication which is accomplished via distinct type of one-to-one connection which provides single path between two endpoints whereas Point-to-multipoint communication is a type of communication offering many paths from a single location to multiple locations.
Network Monitoring (NMS)
Network monitoring is a process where all networking components like firewalls, routers, switches, servers, wi-fi and VMs which are monitored and evaluated continuously to maintain & optimize their availability.
Cyber Security (PT, WAF, PAM)
Cybersecurity is the protection of computer systems and networks from the theft or damage to electronic data, software or hardware as well as from the misuse or disruption of the services offered by an organization.